Rather than logging onto your 3PAR with local user accounts you can use AD to authenticate users and determine what rights they have within the system. We will look at 2 ways of getting LDAP authentication setup, first using the 3PAR SSMC and second using the CLI. In the CLI section I will provide a script you can just modify to get AD authentication setup nice and easily for you.
SSMC Method
1 Open up SSMC for the system you wish to work on
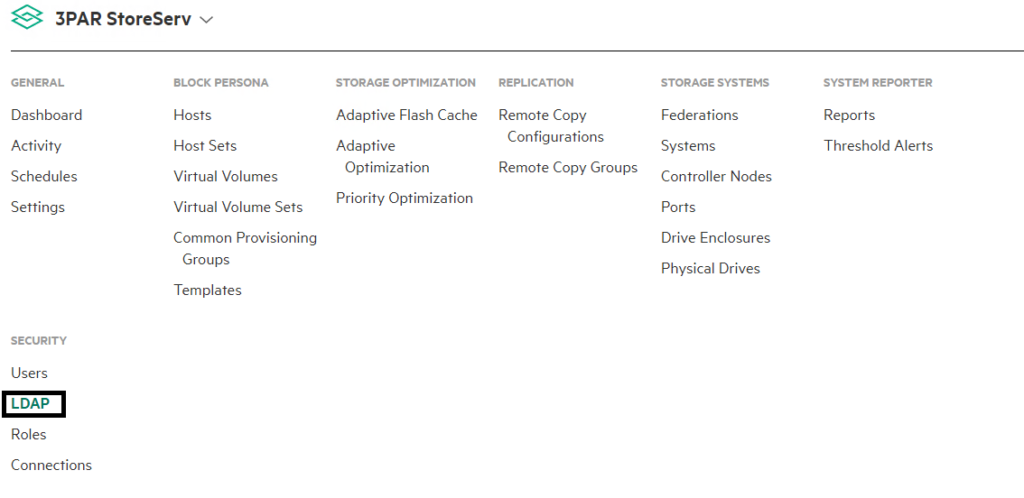
2 Open the main menu and choose LDAP, from the security submenu. If you cannot see it click show more on the far right of the main menu
3 Once in the LDAP screen, from the actions menu on the right of the screen click create
4 You will see a dialog box appear where you fill out all your LDAP details.
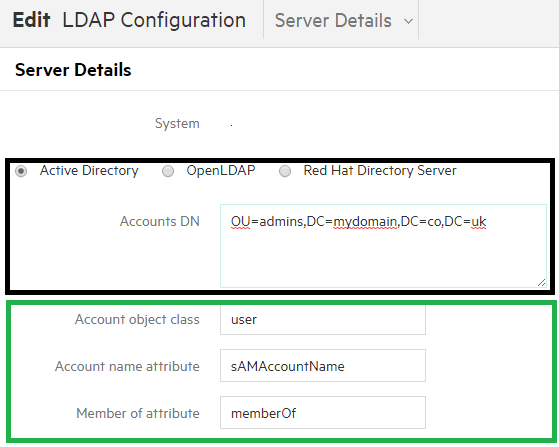
- The first section is Server Details. Choose Active Directory.
- Then in the Accounts DN box below enter the distinguished name of the base location for your user accounts in AD
- The next set of options I have highlighted in green to show that you can these can be set to be the AD defaults as shown in the screenshot below
- Account object class = user
- Account Name Attribute = sAMAccountName
- Member of attribute = memberOf
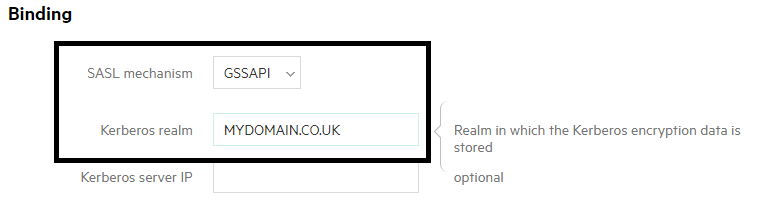
5 In the binding section
- In the SASL mechanism choose GSSAPI from the drop down menu
- Set the Kerberos realm to the realm in which your Kerberos information is stored
- The Kerberos server IP field is optional
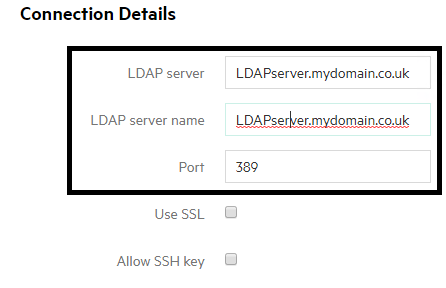
6 In the connection details section
- LDAP server – the DNS name of your LDAP server as long as you are running 3PAR OS 3.1.2 or above. If running a version earlier than this you will need to enter the IP address of your LDAP server instead
- LDAP server name – If you entered the DNS name of your LDAP server above this will be automatically populated
6 That’s the actual LDAP setup complete, now you just need to choose which accounts have access. Access is based on looking up an AD group, you will need to provide the AD group you wish to give access
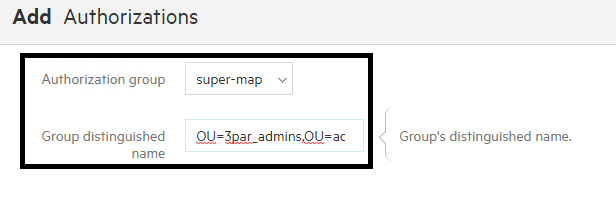
- In the Authorization section click add authorizations
- For Authorization group choose the level of access you wish to grant browse-map for read only, super-map for admin access
- In group distinguished name enter the DN of the group you wish to grant access
CLI Method
Viewing Current Configuration
Show the current authentication settings
showauthparam
If you want to clear out all current settings and start again
setauthparam –f –clearall
Commands Breakdown
The commands you are going to run will fall under three sections; configuring the connection parameters, configuring the binding (authentication) parameters and finally configuring the account location parameters. I have made the text bold to show the commands you would need to customise for your environment, the other commands will remain standard.
1 Connection settings
- IP address of DC that will handle authentication setauthparam ldap-server <IP_address of DC>
- DNS hostname of DC used for authentication setauthparam ldap-server-hn <DNS_HostName
- Set Kerberos realm (domain name) setauthparam kerberos-realm <LDAP_ServiceName eg MYDOMAIN.COM>
2 Configure authentication parameters. These commands won’t change and will just be as below in a standard AD implementation
- setauthparam binding sasl
- setauthparam sasl-mechanism GSSAPI
3 Configure account parameters
- Location of user accounts setauthparam accounts-dn <dn_path eg “OU=Users,DC=mydomain,DC=com >
- setauthparam account-obj user
- setauthparam -f account-name-attr sAMAccountName
- setauthparam memberof-attr memberOf
- Provides Super user rights to the specified group setauthparam super-map “CN=3ParAdministrators,OU=groups,DC=mydomain,DC=com”
- Provides browse user rights to the specified group setauthparam browse-map “CN=3ParRead,OU=groups,DC=mydomain,DC=com”
AD Script
Below I have laid out all the commands together in an example script. As always please use at your own risk and note the first line of code clears out your current authentication configuration. The parts in bold are what you will need to change, everything else should remain the same in a standard Windows environment. Make sure your kerberos-realm matches AD (its case sensitive)
Setauthparam -f -clearall setauthparam -f ldap-server 10.10.10.10 setauthparam -f ldap-server-hn DC1.mydomain.com setauthparam -f kerberos-realm MYDOMAIN.COM setauthparam -f binding sasl setauthparam -f sasl-mechanism GSSAPI setauthparam -f accounts-dn “OU=Users,DC=mydomain,DC=com” setauthparam -f account-obj user setauthparam -f account-name-attr sAMAccountName setauthparam -f memberof-attr memberOf setauthparam -f super-map "CN=3ParAdministrators,OU=groups,DC=mydomain,DC=com" setauthparam -f browse-map "CN=3ParRead,OU=groups,DC=mydomain,DC=com"
Check Configuration
Once you have ran the script you can check the results from the CLI by typing checkpassword <username> and then entering your AD password. The system will then return the results of if the LDAP lookup was successful.

Good post, Richard. Just a heads up, the #3 point up top has a copy/paste typo, I think. The 3parRead group is getting authorized for super-map instead of browse-map. Your script has it right, just the step is off.
Good spot, updated. Thanks Chris!
Gladly. When I tried to configure this in the SSMC, it stated that the ldap-server-hn was optional and that ldap-server supported FQDNs and multiple entries as of 3.2.1 MU2, which I’m running. However, when I try to configure it w/o ldap-server-hn and/or with ldap-server using FQDNs, I get “+ internal system error communicating with authentication helper daemon: invalid response”. Have you seen any of this?
Not something that I have seen. Will approve comment to see if any readers have encountered this and can jump in and help.
Hi,
this link could help with the problem: http://3parug.net/viewtopic.php?t=1147&p=5544
[…] https://3pardude.com/2015/03/05/3par-active-directory-ldap/ […]
Thanks You very much…worked like a charm.!
Great, good to hear!
I am able to configure LDAP on 3par and checkpassword is coming normal while using SSH session,but when i am trying to login SSMC with same credentials, Its throwing an error stating that- Failed to authorize user anandanwar on any configured arrays.
Also when through SSMC,when i am trying to checkpassword -it is showing an error- response was not received from the server within 30 seconds.
The following URI’s failed to respond.
02/05/2019 13:54:19
Action:POST URI:/security/REST/ldapviewservice/systems/2FF70002AC01BAEF/ldaps/6d615d32d9317b623338e5df806bcf23/testldapconnection timeout:30 seconds.
Sounds like you have a comms problem between SSMC and your systems