Given the fun and games that many IT departments will have had over the weekend with the weekend with the WannaCrypt ransomeware I wanted to revisit this topic to understand what ransomeware is and what can be done to reduce risk.
Ransomware was first seen in the mid 2000’s and has grown into a prevalent security threat, with TrendMicro reporting they blocked 100 million plus threats between 2015-16.
What is Ransomeware?
Ransomware is essentially a hijack of the users of machine, that renders it unusable or operating at reduced capacity unless a payment is made. The hijacks fall into two main types of attack, a lockout screen which stops the users accessing any elements of the system until payment is made. In the second type of attack the users files are encrypted and again a ransom is demanded but this time to decrypt the files. The prevalence of these sort of attacks is unfortunately directly linked to that fact they have proved to be a highly effective business for the criminals behind them. We storage administrators have known for some time that both users and organisations data is critically important to them, now unfortunately it seems so do criminals and they are willing to cash in. ZDNet estimated based on Bitcoin transaction information that between 15 October and 18 December CryptoLocker had been used to extort $27 million from victims.
WannaCrypt
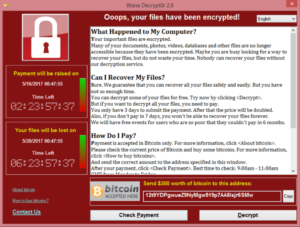
WannaCrypt hit towards the end of last week and so far cases have been recorded in 150 countries. It is a worm that spreads across networks by exploiting a bug in the MS SMB file sharing protocol, once infected the ransomware demands $300 worth of Bitcoins in order to be able to access the system again. The exploit had been previously identified by Microsoft and a patch released in March for supported OS. Of course this meant that legacy systems to such as XP and server 2003 did not receive the patch. Large uses of these legacy systems such as the NHS in England where particularly badly hit, with 48 different trusts reporting issues. Since this time MS have also released the patch to cover legacy systems XP and Server 2003.
Reducing Risk
Given that this is a storage focused blog I wanted to look at the specific considerations around backup given that this is the predominant recovery method. It is an important consideration that the encryption type software will look to encrypt all attached local and network drives. The behaviour of encrypting network shares can be particularly damaging to organisation and is why it is important that users are given the most restrictive rights possible so that the ransomware cannot execute. The importance of staying current and patching has been brought home with the recent WannaCrypt attacks.
Ransomeware Backup Considerations
Replication is not backup – Sometimes high availability and backup are confused. Replication is not backup and ransomware is a good example of why not. If the primary end becomes infected, so will the target once replication is compete. Bear in mind this would include automatic backup to the cloud services.
Hold an offline copy of data – Whilst there have been no confirmed cases of backup software getting hit by an attack ,it is a sensible precaution to protect against a future variant by keeping a backup copy offline or at least in a separate media form. This is in accordance with the standard good practice laid out in the 3-2-1 rule, have 3 copies of your data, 2 different types of media and one offsite copy.
RPO becomes key – With the random nature of these attacks and the potential level of destruction with multiple key file shares potentially being rendered unusable by a single users, how much data can you afford to lose? For those shares which you consider to be at greater risk perhaps due to the number of users you could consider a shorter RPO. Read this article to learn more about selecting an effective RPO and RTO. It may be time to look at more regular snapshot based back ups
Number of Recovery points – The number of recovery points and retention policy also needs to be considered. If you are using a simple policy of 14 days for example it is possible that an infrequently used share, such as one containing monthly finance reporting may only be noticed by a when time all the backups also contain the encrypted files.
Endpoint backup – If users save files locally to their desktop / laptop consider endpoint protection such as Mozzy or Veeam End point protection to safeguard these devices.
[…] Read more at: Ransomeware and Backup Considerations […]
[…] Ransomware and Backup Considerations by Richard T Arnold […]
[…] Ransomware and Backup Considerations – by Richard T. Arnold […]